Filtering (Fake) Phishing Emails
There are times throughout the year at work when I will unknowingly be subjected to red team testing in the form of phishing email attempts. These are vital in validating an organization's ability to detect and respond to unfriendly actors attempting to gain access to unauthorized data. While keeping these detection skills sharp is critical, what follows is how I've mostly automated the detection of these red team phishing campaigns.
Consider the following email:
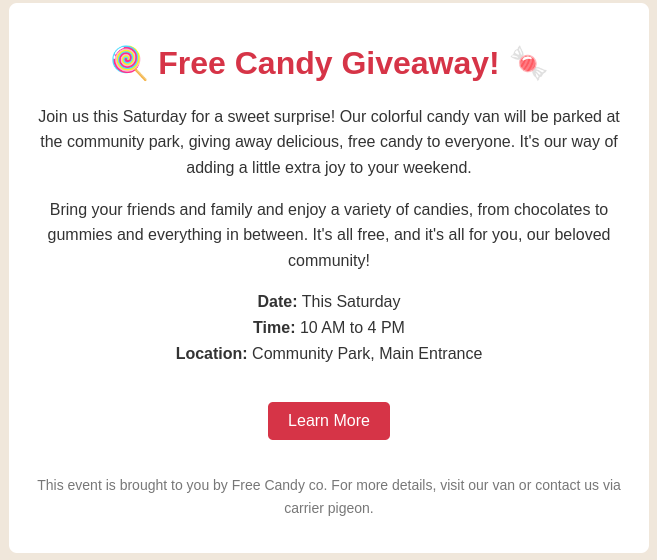
Free Candy
Upon inspecting the email source you may notice a trend in red team phishing campaigns: identifiable metadata!
1Return-Path: <test@local.com>
2Subject: Do you want some free candy
3To: "Chris Zietlow" <aczietlow@gmail.com>
4
5X-Mailer: gophish
6X-Gophish-Header: http://localhost:8080?rid=WYArRwS-gophish
7X-Gophish: True
8X-PHISH: True
9X-PHISHTEST
10
11<!DOCTYPE html>
12<html lang=3D"en">
13<head>
14 <meta charset=3D"UTF-8">
Automating an email filter to check red team phishing email campaigns may or may not be good advice. Proceed with caution and wisdom.
Creating an Email Filter
For my own quality of life I create email filters to label and mark these emails are read when they are received.
Gmail (Google Mail)
There is no simple way to create advanced filters in gmail based on header info contained with the email itself in gmail. To accomplish this we'll need to do the following.
Create a Custom App Script
- Navigate to script.google.com
Start a new project
- Create a script
Write a script a search through your inbox for messages with the specific headers, label them, and mark them as read.
1function labelFakePhishing() {
2 // Search for new email threads
3 let query = 'label:inbox newer_than:1d';
4 let threads = GmailApp.search(query);
5 /*
6 Note that Gmail will group messges (emails) together into a collection under a single subject line referred to as a "thread"
7 */
8
9 let phishingHeader = 'X-Gophish'
10
11 // Create a label.
12 let label = GmailApp.createLabel('A TRAP');
13
14 // Iterate through all messages in the threads returned via the above query.
15 for (let i = 0; i < threads.length; i++) {
16 let messages = threads[i].getMessages();
17 for (let j = 0; j < messages.length; j++) {
18 let message = messages[j];
19 let rawContent = message.getRawContent();
20 // Check the message source for the pressence of the "phishingHeader"
21 if (rawContent.includes(phishingHeader)) {
22 GmailApp.moveThreadToArchive(threads[i]);
23 label.addToThread(threads[i]);
24 }
25 }
26 }
27}
For additional information see the GmailApp API.
- Create a Trigger
In order to run the script automatically, set up a time-based tripper.
- Click the clock icon in the left panel
- Click "Add" trigger
- Set up the trigger to run the function. (e.g.
labelFakePhishing())
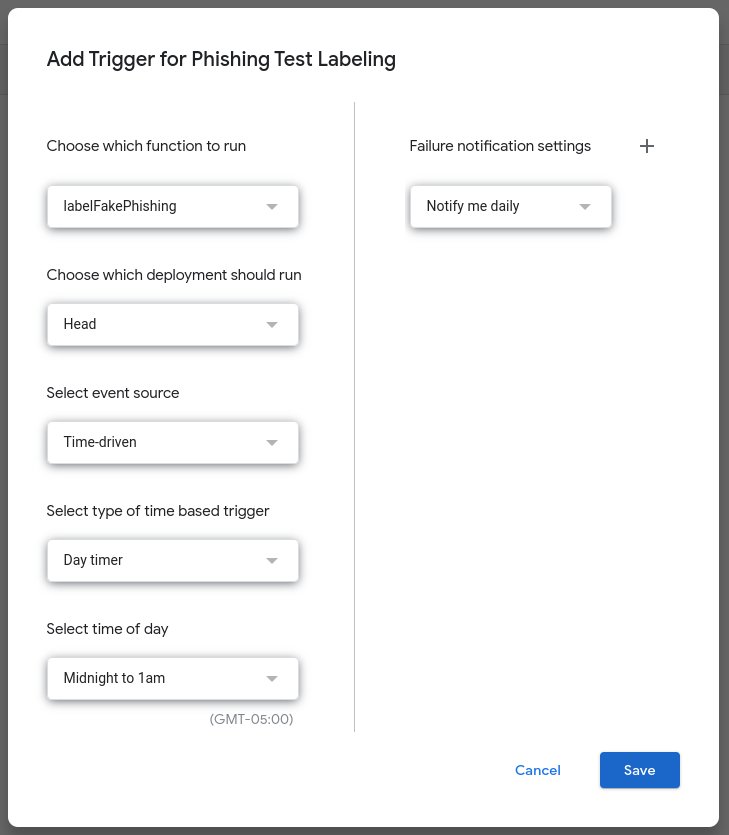
Google App Script Trigger
- Permissions
The first time you run the script, you will need to authorize it to your Gmail account
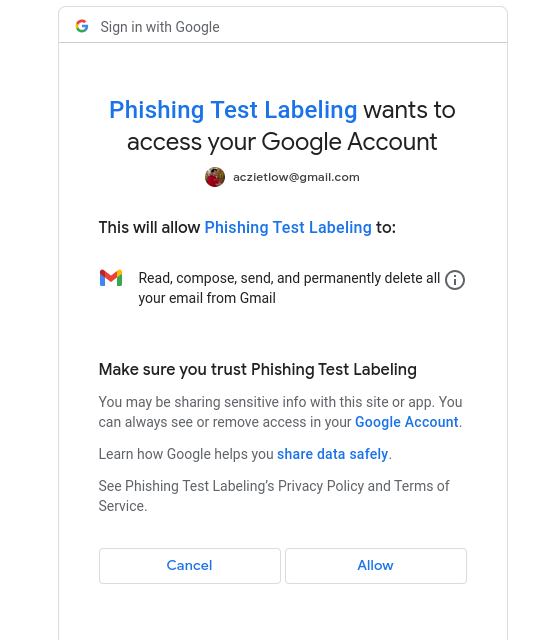
Google App Script Auth
- Victory!K
Now phishing emails are labeled with my custom "It's a Trap!" label and moved out of my inbox.
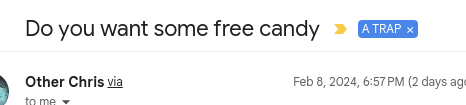
Labels in Gmail
Outlook
- Open Outlook
- Navigate to the Home tab
- Click 'Rules' > 'Manage Rules & Alerts'
- Create a new Rule
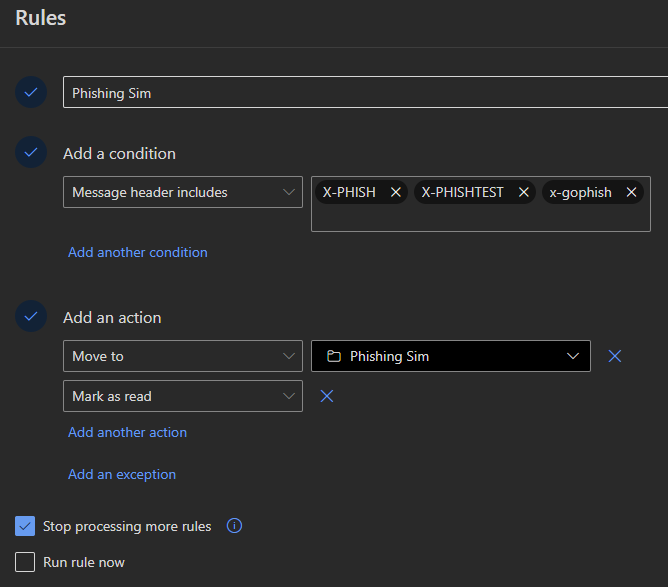
Outlook
Considerations
If there is ever a sliver of doubt, one of the first things I will do is view the source of the email in question. There are a few low-hanging fruit that can help to identify phishing emails such as poor grammar, clearly malicious URLs, or the deposed prince of Nigeria asking for money. A few higher value validations I prefer to review is if the mail in question has valid DKIM, DMARC, and SPF records. Malicious actors can and will attempt to spoof the domain an email is actually coming from.
None of this is intended to be a panacea. Creating filters to bypass practice these skills may in fact lull your awareness and readiness for these kinds of attack vectors in the future. Again, I want to stress the use of caution and wisdom in implementing something like this. For me it was a small quality of life improvement in response to a now former customer with an overzealous red team. If that is the case for you, I'd encourage you to try the same.
As always stay alert and vigilant.
This post's permalink is https://zietlow.io/posts/2024/filtering-phishing-emails/ and has the following summary:
There are times throughout the year at work when I will unknowingly be subjected to red team testing in the form of phishing email attempts. These are vital in validating an organization's ability to detect and respond to unfriendly actors attempting to gain access to unauthorized data. While keeping these detection …
The canonical URL for this post is https://zietlow.io/posts/2024/filtering-phishing-emails/
